
If you are a complete security newbie and struggle to talk about security technology at all, or get value across when talking to customers or colleagues, this is for you.
————
If you have experience of trying to explain ‘Cyber’ security, you will be aware of how difficult it is to get the value of security across to those with little knowledge, other than a general feeling that “Security is something important that we appear to need, right?”.
The aim should not be to explain exactly what Security is (good luck with that), but why it matters, and matters to them.
Security metaphors, (and there are lots of them), though limited, have their uses. The idea is simple. If you can relate cyber security to something familiar, you are off and running.
The aim is to be able to explain to anyone in 30 seconds why it is important without confusing them. If you have done this right and ignited interest, you can then move onto specifics and deeper conversations. For example:
Imagine coming home and you are sure someone has been in your house! However, you can’t place whether anything is missing, not sure what has been touched, no idea how they got in, who it was, or whether they will be back? (or even if they are lurking in a cupboard sitting tight). It is unlikely you will lock up, go to bed, and never think about it again. This is the situation many businesses currently find themselves in, and some don’t know where to start. It is an ever changing and complex digital world we live in.
The House/Home
Some Cyber security purists dislike the ‘House’ or ‘Home’ comparison, because it is not a straight enough analogy and misses out a number of important ‘Cyber’ or digital security concepts. This is a perfectly valid viewpoint. Remember though, the intention here is not to explain to Cyber security purists, but to relate the importance of security to anyone.. As long as you understand some of the shortcomings it can be a useful tool.
Your house is a good example of the balance between Security and Usability.
Nobody has a perfectly secure house or home, and for good reason. If you wish, you can certainly make it pretty secure with enough money. You can build your home as a fortified concrete bunker on an Island in the middle of the Atlantic, without windows or doors, complete with standing army, air & sea defense, and your own delta-force for counter moves. For home-life however you really need to interact with the real world. There is community, your job, getting the kids to school/clubs, food, leisure, happiness, on and on. So we need a balance. Security is always a trade-off.
with enough money. You can build your home as a fortified concrete bunker on an Island in the middle of the Atlantic, without windows or doors, complete with standing army, air & sea defense, and your own delta-force for counter moves. For home-life however you really need to interact with the real world. There is community, your job, getting the kids to school/clubs, food, leisure, happiness, on and on. So we need a balance. Security is always a trade-off.
The same is true with ‘Cyber’ security. Knowing where to draw the line and find a balance is key. How do you secure your digital business without getting in the way or slowing things down? This is a Risk conversation pure and simple.
Homes are designed to be functional. We don’t use the most secure materials to build them (e.g bricks, mortar, wood, glass etc.). We take into account aesthetics, large windows to let the light in, open views, large welcoming doors with letter boxes etc. In fact we prioritise usability and aesthetics over security every time, and rightly so. We have lives to live, need easy access, take shopping deliveries, welcome family and friends. The priority is our need for comfortable, functional living. In turn we accept this exposes us to a number of threats. We know our homes and what is inside them has value, so in response we put some security measures in place. The key is to make it robust without impinging on our lifestyle… to think bigger picture. Balance.
At the risk of repetition, security at all costs will not enable us to achieve the functional liveable space we desire. Human nature also makes it naive to think we don’t default to similar ease-of-use priorities in business.
Prediction, Detection, Prevention and Response
We naturally accept that our homes can be broken into. Given this we look at what goes on in wider society and take advice from specialists (Police etc.) to predict the kind of things that might happen, or are a likely threat in our location. We have access to crime statistics, patterns relating to our demographic, and look for things of concern. For example, you are significantly more likely to be burgled in the immediate weeks following a neighbour’s burglary.
We try to prevent unauthorised access, by establishing a perimeter with surrounding fences, garden walls, and the walls of our homes. We provide controlled perimeter access through gates and doors, using good locks for legitimate access (a bit like passwords in the cyber realm). Windows are installed for light, air, and aesthetics, but can also be dual-used for illegitimate access, so we close and lock them when no-one is around to monitor.
There is lot of activity back and forth through the perimeter of our homes, so we try to let the harmless flow unimpeded while limiting the harmful. Firewalls enable this function in the ‘cyber’ world. There is an amount of monitoring through neighbourhood watch schemes, relationships with neighbours, and local police patrols perhaps logging suspicious activity. We want to know what has gone on. In the digital world we log and monitor our platforms at scale through SIEM (Security Information and Event Monitoring) taking in all the info/logs from Firewalls and infrastructure, with additional threat-feeds that you and others have identified. Continuous Monitoring.
Maybe we use motion lighting on the outside of our house, with visible cameras or even a large alert-dog to help detect a threat and act as a deterrent.
House alarms are installed to detect and alert if someone has broken into the house (through sounding alarms, or by contacting the owner or law enforcement), giving some opportunity to respond in real-time. Detecting a breach, much like intrusion detection systems or IDS with events and alarms.
We remain alert and vigilant for anyone in our home who shouldn’t be there, and respond appropriately. This could be through alarming intruders (letting them know you are there), or alerting the police and waiting for help to arrive Once an incident is over we respond by thinking what we can do to prevent a repeat occurrence. Incident response
We security mark valuable possessions so they are difficult to sell-on and reduce their stolen value. Assess our most valuable possessions and put additional security controls around these – put them somewhere safe, maybe literally in a safe. Asset security.
Even then there remains uncertainty. Have we appropriately addressed the risk? A course of action might be to outsource some of the “What happens if?” by paying experts in risk assessment through insurance (let’s face it, if insurance companies were bad at assessing risk they wouldn’t be in business for too long).
Ultimately we know and accept it can happen so look to minimise loss if it does. We take much of this for granted in every day life so why is there often a blind spot in business? Maybe because it is less personal, or organisational complexity in the digital world makes it much harder to visualise? Either way the same mind-set should be applied.
It just so happens this analogy closely aligns to Gartner’s Adaptive Security Architecture that most security professionals are familiar with. In fact when choosing products or functionalities it can pay to identify under which category they might sit.

It is the thought process that is important here, not the technology. Many have relevance in some or all parts of the wheel.
So how do we assess what we need for our homes or business?
At home, without thinking too hard about it, we assess the risk. All security professionals know that a risk based approach pays dividends. Understanding your metaphorical controls for home security is a good place to start when trying to relate to what a business needs.
Risk = Threat x Vulnerability
Most know their basic home threats and vulnerabilities through general awareness. You might know roughly the crime-rate in your area, number of burglaries etc. You might also know some of your vulnerabilities e.g. doors, windows, inadequate lighting, no alarms, hidden access etc. and have taken steps to make each more robust. Extending these ideas more methodically to business just makes sense, and needs to become instinctive. The good news is that the principles of risk management and processes you already use apply equally to Cyber Security.
Your business probably has a risk matrix for all manner of things, you just need to know how to apply it to the digital world. How you asses ‘cyber’ risk might be based on a likelihood and impact risk matrix into which you plug your assessments. Identify your threats, number them against your vulnerabilities, and then feed into a matrix. Assets and asset value also feed into this risk calculation with frequency, cost and consequence of impact.
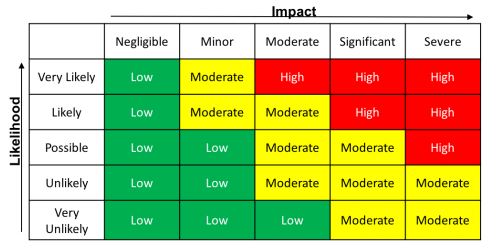
What can we do with this Risk once quantified? There are broadly 4 choices:
- Accept the Risk
- Avoid the Risk
- Transfer or outsource the risk
- Mitigate the risk
(you can also exploit the risk if positive to your business, but most security risks favour the negative)
It is fair to say not many people go to this level of detail with their homes. Maybe they should?
Security as an integrated platform.
There are a dizzying array of products offering magical security powers to solve security problems. There are many to be solved. The Cyber security industry thrives precisely because we are discovering new problems all the time, and the ones we know about are difficult. Of course, wherever there is uncertainty and high demand you get your fair share of ‘snake-oil’ salesman looking to capitalise. Just as in the real world there are opportunistic ambulance chasers following reams of alarmist news. All this noise makes it doubly hard to separate what’s actually of concern to you and your business.
So how do you choose what is right for you?
First it is worth remembering there is no magic pill to cure all security illnesses for evermore.
Just like with the home, it helps to take a wider view. Security is determined much more by what you do than what you buy. If you leave the doors and windows open or tell the world you will not be home for 3 weeks, your risk goes up. If you have good security awareness and behaviour, aligned to recommended security systems, your risk goes down. Identify the behaviours and functionalities you need to lower your specific risks and focus on these.

Zero’ing in on your threats and vulnerabilities to inform your risk, is a great place to start. Services that give visibility of relevant internal and external threats, and something that can do the same for internal and external vulnerabilities, (with human-in-the-loop context) and making these specific to your organisation, are a good way to identify where to focus your efforts and spend. Establish your security posture
Integrated, embedded security platforms and architectures tend to work better than many point products weaved together in a security patchwork (Why else do you see all your favourite security vendors waxing lyrical about fabrics and platforms?). That is not to say complex security patchworks can’t work, but you really need to be on top of your RACI matrix and understand all your dependencies.
We are aiming for a robust operational security program that quickly detects, responds and minimises loss. Security need to be agile enough to take appropriate business risks to interact and compete in the marketplace. Like our homes we want a secure and usable environment by design.
If we can understand our risk properly, deploy defense in depth, while relentlessly focusing on the real-life goal of security and usability we will be half-way there.
But the walls are breaking down?

As the four walls of the digital home or castle have broken down recently in a world of mobile devices, Cloud and IOT, so too does the analogy. We are being forced to secure data and applications anywhere with zero-trust. Does this mean we are helpless? Of course not. Just as we keep ourselves as safe and secure as possible while roaming the modern world, so too must our business. We cross roads at crossings, look around with our heads up aware of signs of danger (not staring into our mobile phones on busy streets?). We don’t leave nightclubs alone, avoid dark alleys, lock our cars, keep our wallets and purses hidden and close to us, and maybe even take the odd self defence class. We rely on a broader public infrastructure; emergency services, CCTV, daily vigilance and reporting suspicious items or behaviour etc. Similar techniques are used in the digital world as well, aware of the risks of our new surroundings.
We protect data inside and outside of our business walls through encryption, in transit, at rest and in memory. We don’t keep things on show. We make sure only those who are allowed have access to what they need when they need it – Identity and Access Management (IAM) again. Logging and recording all the things for analysis and audit, and making sense of what has happened and what might happen through correlation and intelligence in the cloud and beyond.
Regardless of environment I would always encourage a wide ranging understanding on as deep a level as you can. Don’t be afraid of technology as much of it can be related to the real world.
You don’t need to be a security expert to make good security decisions. You don’t always understand technically how a fancy alarm system works, but you know why you have it, and what to do when it goes off.
Understanding what you are trying to achieve and why, is essential even if you ultimately defer to a specialist to tell you “how”. Taking the time to understand your own threat landscape and vulnerabilities while relating to the real world, makes deeper conversations more accessible to everyone.
———
Like security metaphors? 32 of the best and worst here

Know your Analogies from your Metaphors and Similes?
…want to start your security journey with some very basic key concepts? See below:
———–
a few caveats…
There are way too many to mention as all analogies break down at some point when dealing with complexity, but I would like to mention a few differences/concepts that exist in the digital world that are useful to carry around.
Firstly class-breaks. Class-breaks take a vulnerability that breaks not just one system but an entire class of system. If you need to manually pick every lock then that would take time, but if you found a single vulnerability in all locks, you have yourself a class-break. This is the way computer systems fail, but not how many people think of failure. In the computing world it might take one person to figure out how to attack a system, then write software to automate the attack and you can then take advantage at scale almost instantaneously.
Another example: If I wanted to steal information (personal or otherwise) from your paperwork draw, filing cabinet, or rubbish bin, then I would have to rummage around in each one manually. How long would it take to do this for an entire neighbourhood, company, town or city? Again, the digital realm enables you to do this at scale, almost instantaneously.
I am sure you can imagine many other limitations to the home analogy. Physical constraints; burglars can only go one house at a time, through one entry point typically, as opposed to multiple on a network. They only take what they can carry, only get value when they remove something once in the house, and they can be prosecuted easily and locally when caught. They typically don’t gain entrance pretending to be one of the family, or hide in your house for months, and can have wildly different motives. Home security is also not focused on protecting against corporate espionage, direct political action, or nation-state actors. There are many more.
Remember we are not searching for a perfect analogy, but rather making security familiar enough for discussion at all levels of an organisation, so everyone can see the importance and relate to your plans. The more people who engage, the more secure we all will be.

